What do employers want in a DevSecOps engineer?
A semi-scientific statistical analysis of Job requirements in adverts
DevSecOps, an ill-defined term at best, and a complete mystery at worst.
As someone whose entire job comes down to figuring out ‘what kind of DevSecOps engineer are you/are you looking for?’ it’s something I think about a lot.
DevOps itself is a methodology not a title, so what happens when we start adding security into the mix? The short answer is, that DevSecOps is tricky to define.
Is it a Security Engineer who can code?
Is it a DevOps engineer who knows some security?
Is it a catch-all term for anyone who knows a bit of infra and a bit of security?
Is it just a methodology too, the Shifting left of security in the DevOps pipeline?
Every team out there would define DevSecOps as something different, every team uses a different tech stack, and every team runs security slightly differently in their org.
So if you’re a junior looking to get into this space, or a CTO looking to make their first hire into a startup, how the hell do you know what tech to focus on?
Trying to Objectify the Subjective
With all these different opinions on what a DevSecOps engineer is, I thought I’d try and focus purely on the requirements I’m seeing across a series of job adverts, 200 to be exact.
I took these 200 Job Adverts from LinkedIn ads and other Job Boards covering roles in the EU and US.
With these, I then categorised some of the more frequently seen tech, tools, certifications, and general requirements then manually counted which of these 200 adverts mentioned the item at least once in their ‘Preferred Requirements’ ‘About you’ or ‘Nice To have’ sections.
The Categories were:
Amazon Services (AWS)
Azure
Google Cloud Platform (GCP)
CI/CD Tools — Any mention of specific tools or CI/CD in General
Container Tooling — Kubernetes, Docker, Openshift, ECS or any managed container service
Dev Skills — Requesting experience with a specific programming Language
IaC — Teraform, CloudFormation or any mention of Infrastructure as Code
Cloud Or DevOps Cert — A Specific Cert Requested for a DevOps/Infra tool, or saying ‘Any Cloud Certificate’
Security Specific Cert — Same as above but for CloudSec or General Sec Tooling
PenTesting — Experience in Penetration Testing or Specific PenTest tools
Sec Scanning (DAST/SAST) — Again, Tools or mention of it
Threat Modelling — Any requirement for this experience or mention of experience with common threat modelling frameworks i.e MITRE ATT&CK
Security Framework Knowledge- SOC 2, ISO 27001, NIST, HIPAA, PCI etc.
IAM — Any mention of Identity and Access Management experience
Degree — Any Bachelors or Masters Degree
The Results
So what did I learn? For one, there are some very poorly written adverts out there. Many skipped mentioning a tech stack entirely, some listed tech in the ‘nice to have’ and in the ‘requirements’ and some were a bullet point list with no text at all.
In general I stuck to adverts that had a good description and a clear list of tech requirements. I also discounted any adverts that were repeats, i.e the same company hiring multiple engineers of the same seniority in different locations.
What did the numbers reveal?
DevOps is King
DevOps tools dominated the rankings, with the vast majority of adverts requesting some kind of tech or tools typically associated with a DevOps or Infrastructure role.
CI/CD tooling was the most common by far, with 82% of Adverts requiring experience with it to some degree.
The most commonly used cloud provider was AWS with 68.5% of adverts using it, although it is tricky to track as many ads mention multiple providers, and rarely distinguish which is used internally and what is just an example.
Container tooling was unsurprisingly also high up the rankings, with nearly two-thirds of the adverts requesting experience with implementation, or even security within Container environments.
One of the more surprising ones was the number of posts requiring DevSecOps engineers to be able to code. For this, I counted Java, Python, Go, Ruby, C, C++, C#, JavaScript (and its flavours), and Rust.
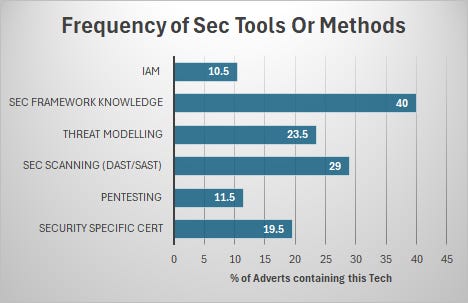
Sec Tooling took a back seat
In a lot of the articles ‘Experience with security’ was about as specific as it got, with many others describing what I’d personally consider a purely DevOps role.
For those that delved a bit deeper, many couldn’t describe well what the security function did outside of a few buzzwords.
The most common buzzwords? Security frameworks. Either specific ones or asking for security framework knowledge in general. This was in 40% of the adverts.
Pentesting was in only 11.5% of ads which is small, but this makes sense. The majority of companies would have specific Red Teams for this, or in the case of Startup Teams, perhaps would bring on a consultant to run some tests.
Implementation of security scanning tools was only in one-third of adverts which I felt was surprisingly low, given this enables the ‘shifting left of security’ in the pipeline, which is one of the definitions of what a DevSecOps engineer enables.
Certifications — Don’t bother
The security industry is well known for being a sector where people parade around their certificates like medals, with DevOps heading the same way.
If you’re a grad looking to spend some bucks on a certificate so it will ‘guarantee you better job prospects’ I’d reconsider.
Only 1 in 5 Adverts listed a cert as either a hard requirement or a ‘nice to have’.
On top of this, anecdotally, many of the security leaders I speak to day to day are exhausted with the number of candidates they receive that have multiple certifications in an area, but very little hands-on practical experience.
Why are people still requiring these?
Bachelors and even Masters degrees were listed as a requirement in too many jobs.
I’ve posted about this on LinkedIn before but if a company is genuinely focusing on Diversity and Inclusion, limiting applications to only those who have been able to afford expensive higher education is prohibitive to this.
Everyone knows the stories of all the famous college dropouts who have gone on to found billion-dollar companies, and I bet everyone reading this article knows multiple self-taught engineers who have been invaluable in building their teams.
I know the common arguments, such as some consultancies that work for governments needing them, or people wanting candidates to have a base level of knowledge. My simple counter is that a university can often be like a giant certification, it's no substitute for on-the-job learning, and governments should recognise this too.
Let's do better.
The conclusions and advice
To summarise, DevSecOps is a wildly misunderstood term with many different definitions, making it very tricky to hire for, and very tricky to break into without industry knowledge.
So what tech should you focus on if you’re looking to become a DevSecOps engineer?
CI/CD Tooling — With it being in the majority of ads, getting some experience in a DevOps role dealing with pipelines makes sense as a first step.
Cloud- AWS is the most commonly used, but as many cloud providers you can get hands-on experience with the better.
Avoid Certifications — Save your money and time, maybe do some side projects or a small part-time gig instead.
Learn some security frameworks — With many teams trying to adhere to a framework, and with it being a nice recognisable buzzword, it is something good to add to a CV, plus, it’ll genuinely help.
Make your experience in an area clear to those who might not know the tech— If you have used Burp Suite, put it under a DAST section, if you have used Wire Shark put it in a PenTesting section. A good internal recruiter should know what the tools do, but make it clear as day in case they’re recruiting in an area they don’t know much about.
What should you do if you’re looking to hire a DevSecOps Engineer?
List your Tech requirements clearly — People can rule themselves in or out from there, saving yourself time
Know what you’re trying to achieve with the role- A DevSecOps engineer isn’t needed by every organisation. Set out clear objectives, work out how you’ll measure those, figure out how the engineer fits into your team, and best of all put all this in your advert or Job Description.
Rely on experts if you don’t have knowledge yourself — Security is hard. Utilise the knowledge of friends in the space, maybe bring in a consultant to work hands-on, or even *Shudder* speak to a specialist recruitment consultant to help define the role and responsibilities.
Closing words
To finish it all off, I wanted to make clear that I know this is not the most scientific of analyses, but I hope it can add some value to those trying to navigate this space.
The DevSecOps space is continuously growing, so the sharing of knowledge and opinions in this area benefits everyone.
I also hope this sparks some interest, as I plan to follow up on this with my list of honorable mentions, along with a breakdown of some of the methodological flaws.
I’d love to hear comments, feedback, and suggestions for the future.






Excellent James. I love that you identify all the confusion around DevSecOps. I am tempted to say it is not even a thing. No working definition. Hiring is basically for dev/infra people with security knowledge nice to have.
I feel for all the vendors selling shift-left products. Who do you even target to sell to? The VP Engineering? Does she even have budget for changing the way they do things, and possibly slowing the dev process?